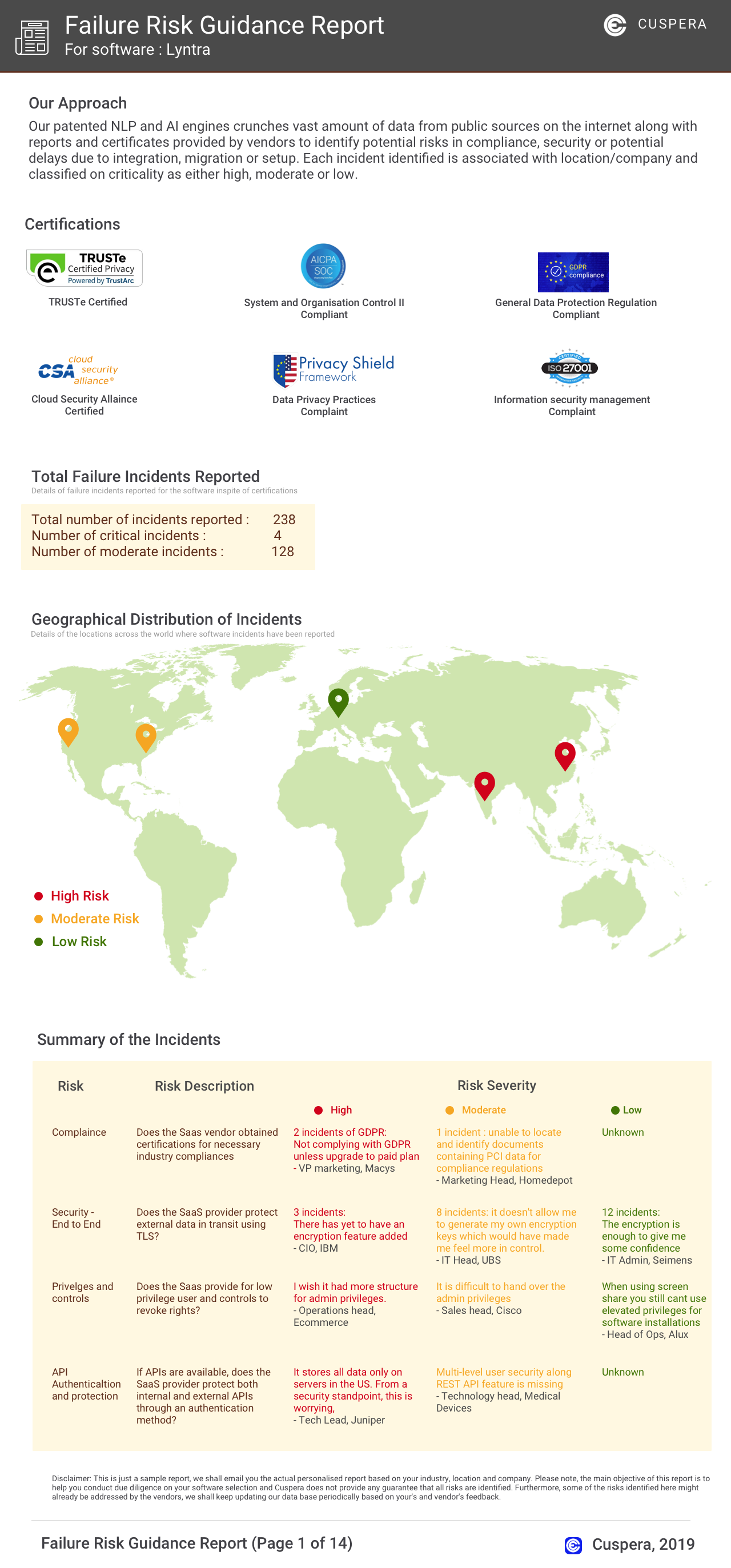
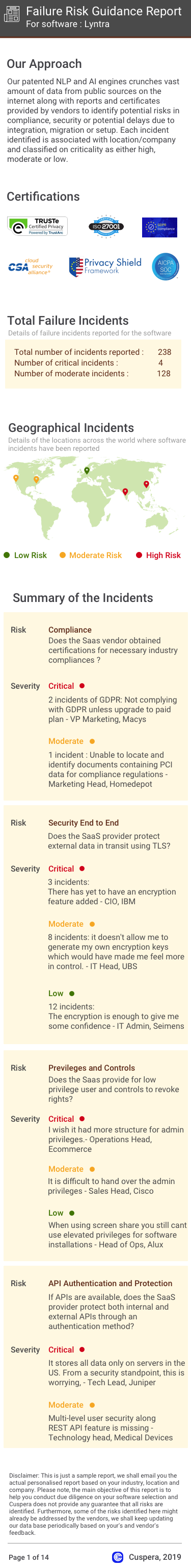
Comparison Summary
This comparison report of FileStack Transform vs. Intercept X Endpoint is based on a specific set of business needs and context. The comparison uses 2141 Cuspera insights based on peer reviews, case studies, testimonials, and expert opinions across 50+ sources.
Introducing FileStack Transform and Intercept X Endpoint
FileStack Transform, and Intercept X Endpoint belong to a category of solutions that help Endpoint Security. Different products excel in different areas, so the best platform for your business will depend on your specific needs and requirements.
FileStack Transform covers Workflow Management, Content Management with Social Media, Sales Document Management, Training & Onboarding with Video, etc.
Intercept X Endpoint focuses on Helpdesk Management with E-Mail, Engagement Management, Groups Management, Lead Tracking, etc.
Unsure which of these solutions is right for you? Our Cuspera AI engine can compare them based on your needs and specific to your industry and context. Get your personalized report today.
 FileStack Transform
FileStack Transform
Focus area
FileStack Transform is better than Intercept X Endpoint for
Software Failure Risk
About
Filestack Transform: Powerful Image Transformations.
Comprehensive endpoint protection and includes options for powerful EDR and XDR security.
Financials
M&A
IPO
Business Need
Total Processes
(we found evidences for)
33
17
Total Goals
(we found evidences for)
6
4
Top Processes
Evidences indicate better relative satisfaction
Top Goals
Goals Achieved
-
Scale best practices
-
Acquire customers
-
Improve efficiency
-
Enhance customer relationships
-
Launch new products
-
Improve ROI
- See 3 more
-
Enhance customer relationships
-
Acquire customers
-
Scale best practices
-
Improve efficiency
- See 1 more
Top Channels
Channels Used
-
e-mail
-
website
-
e-mail
-
website
Failure Risk Guidance Security Report?
Compliance Risk
{{{rsh_C_1}}}
{{{rsh_C_1}}}
Security & Privacy Risk
{{{rsh_C_1}}}
{{{rsh_C_1}}}
Integration Risk
{{{rsh_C_1}}}
{{{rsh_C_1}}}
Migration Risk
{{{rsh_C_1}}}
{{{rsh_C_1}}}
IT and Other Capabilities
- Low
- Medium
- High